|
|
【游戏保护】监视内存页(基址 关键数据)非法访问原理:对内存页面设置PAGE_NOACCESS保护 当程序内访问改页面内数据时产生ACCESS_VIOLATION 产生异常被VEH捕获 VEH处理函数内还原内存页面PAGE_READWRITE属性 然后设置ExceptionInfo->ContextRecord->EFlags |= 0x100 单步异常 返回EXCEPTION_CONTINUE_EXECUTION 程序再次执行 触发单步异常 单步异常处理内再次对内存页面设置PAGE_NOACCESS 等待下次异常访问
用途:检测非法模块 内存监视
可以根据ExceptionAddress 判断异常产生是否位于非法模块
游戏中常用来监视.data段 基址所在内存页
- // Project1.cpp : 此文件包含 "main" 函数。程序执行将在此处开始并结束。
- //#include <iostream>
- #include <Windows.h>
- PVOID Address;LONG WINAPI VectoredHandler(struct _EXCEPTION_POINTERS* ExceptionInfo
- )
- {UNREFERENCED_PARAMETER(ExceptionInfo);DWORD oldProtect=NULL;printf("线程ID %d \n", GetCurrentThreadId());printf("ExceptionCode %x \n", ExceptionInfo->ExceptionRecord->ExceptionCode);printf("ExceptionAddress %x \n", ExceptionInfo->ExceptionRecord->ExceptionAddress);if (ExceptionInfo->ExceptionRecord->ExceptionCode == STATUS_SINGLE_STEP){VirtualProtect(Address, 1024, PAGE_NOACCESS, &oldProtect);}if (ExceptionInfo->ExceptionRecord->ExceptionCode==EXCEPTION_ACCESS_VIOLATION){printf("ExceptionAccessAddress %x \n", ExceptionInfo->ExceptionRecord->ExceptionInformation[1]);if (ExceptionInfo->ExceptionRecord->ExceptionInformation[1]==(DWORD)Address){ExceptionInfo->ContextRecord->EFlags |= 0x100;VirtualProtect(Address, 1024, PAGE_READWRITE, &oldProtect);}}return EXCEPTION_CONTINUE_EXECUTION;
- }int main()
- {DWORD oldProtect = NULL;AddVectoredExceptionHandler(1, VectoredHandler);Sleep(1000);printf("主线程ID %d \n", GetCurrentThreadId());Address=VirtualAlloc(NULL,1024, MEM_COMMIT, PAGE_READWRITE);printf("Address %x \n", Address);VirtualProtect(Address, 1024, PAGE_NOACCESS ,&oldProtect);*(DWORD*)Address = 123456;system("pause");
- }
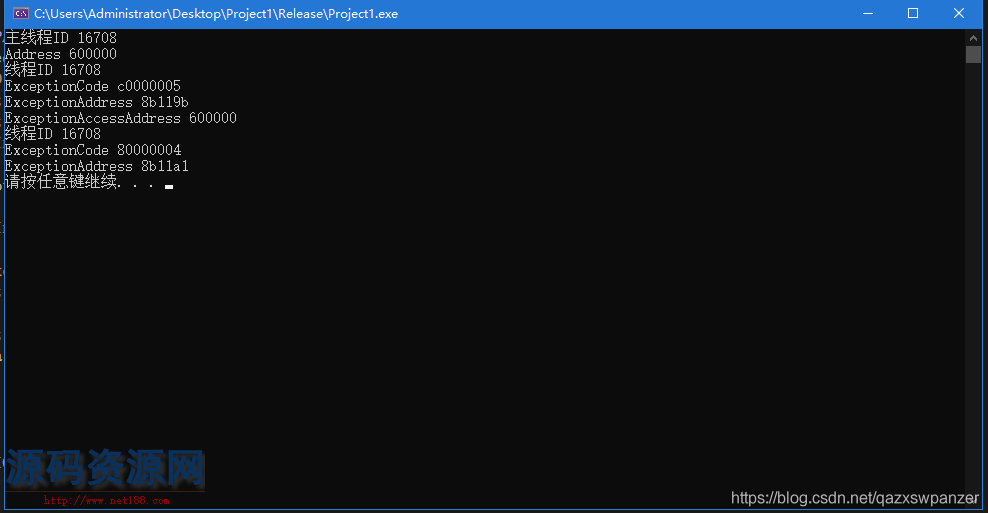
实际效果
正常运行
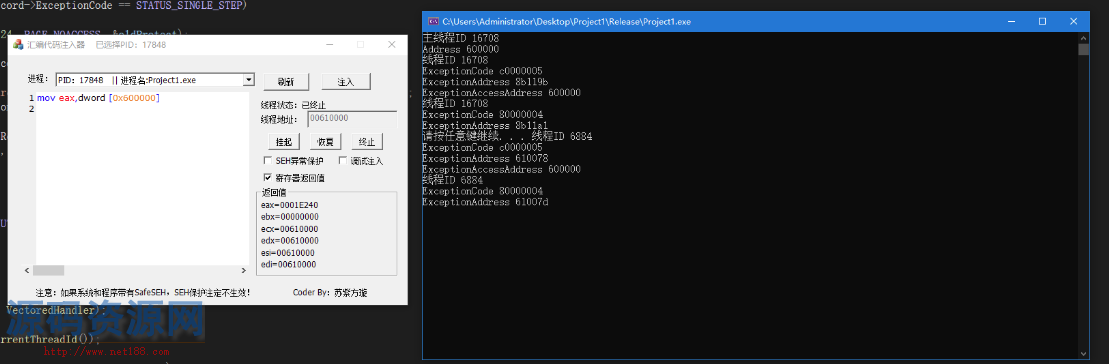
注入代码后
|
|
 |免责声明|小黑屋|依星资源网
( 鲁ICP备2021043233号-3 )|网站地图
|免责声明|小黑屋|依星资源网
( 鲁ICP备2021043233号-3 )|网站地图